Understanding WMI Provider Host
WMI Provider Host, or *, is a legitimate Windows process part of the Windows Management Instrumentation framework. It handles scripts and queries for system management tasks like monitoring hardware or software. While essential, malware can hijack this process, causing confusion and system issues.
Is WMI Provider Host a Virus?
No, * itself is not malware. It is a core system file. However, cybercriminals often exploit WMI to embed malicious code, making it appear as "* virus." Signs of infection include high CPU usage, unexplained network activity, or the process running from abnormal locations.
How to Check for Malware
Confirm if WMI Provider Host is compromised by following these steps:
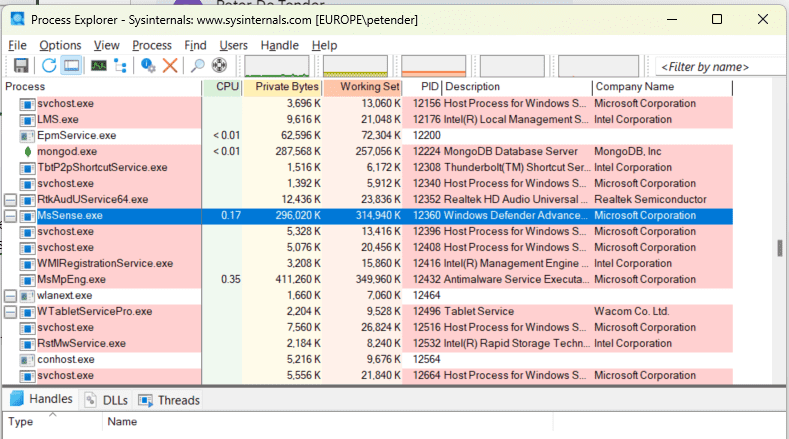
- Verify file location: Legitimate * should reside in "C:WindowsSystem32wbem" or "C:WindowsSysWOW64wbem". If found elsewhere, it may be malware.
- Inspect digital signature: Open Task Manager, right-click *, select Properties > Digital Signatures. Look for Microsoft Corporation as the signer.
- Run security scans: Perform a full system scan using built-in antivirus tools like Windows Defender or reputable third-party software.
- Monitor system behavior: Check for unusual network connections or resource spikes via Task Manager or process analysis tools.
Safe Removal Methods
Eradicate malware safely without damaging your system:
- Boot into Safe Mode: Restart your PC and enter Safe Mode with Networking via Advanced Startup options to prevent malware activation.
- Execute thorough scans: Use antivirus software to detect and quarantine infections. Quarantine results before removal.
- Clean WMI manually: As administrator, run Command Prompt and enter commands like "winmgmt /resetrepository" to restore corrupted components.
- Delete suspicious files: Navigate to identified malicious paths in File Explorer and delete files not signed by Microsoft. Exercise caution to avoid system-critical files.
Prevention Tips
Protect against future infections:
- Update Windows regularly to patch vulnerabilities.
- Install and maintain active antivirus protection.
- Download software only from verified sources.
- Enable firewalls and conduct periodic system scans.