What is SSH Reverse Tunneling?
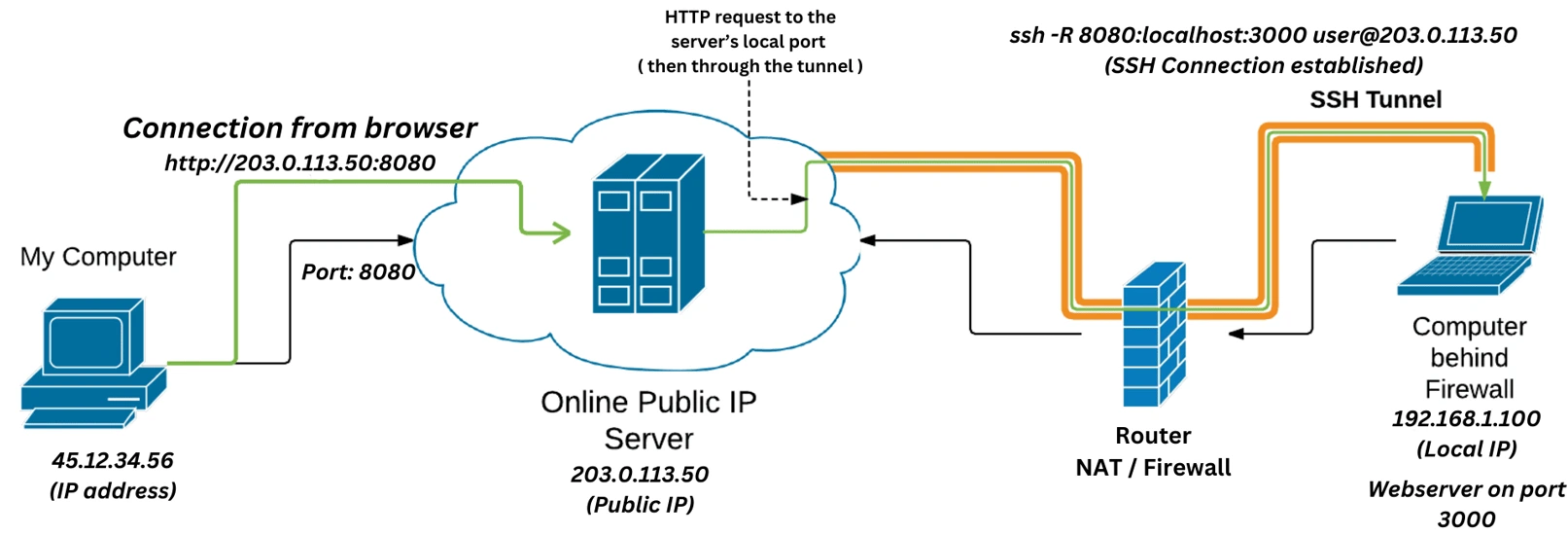
SSH reverse tunneling securely exposes a local service on a remote server to external access over the internet. It's ideal for accessing devices behind firewalls, NATs, or with dynamic IPs, using SSH's port-forwarding feature without 加速器s.
Basic Setup Requirements
- A client machine with the service to expose (e.g., localhost:8080).
- A remote server with public access and SSH connectivity.
- SSH installed on both devices. Commands assume Linux/macOS terminals.
Step-by-Step Implementation
- Step 1: On the client, initiate the tunnel using this command:
ssh -R remote_port:localhost:local_port user@remote_server_ip. Replace with your details.
- Step 2: Connect to the remote server:
ssh user@remote_server_ip. Enter passwords or key credentials if prompted.

- Step 3: Test the tunnel by accessing remote_server_ip:remote_port externally to reach the local service.
Example Use Case
To expose a local web app on port 8080 to a remote server on port 9090:
ssh -R 9090:localhost:8080 user@123.45.67.89. Now, external users navigate to 123.45.67.89:9090 for access.
Essential Tips
- Ensure GatewayPorts is set to yes on the remote SSH server config for broader access.
- Use SSH keys for authentication to avoid password prompts and enhance security.
- Monitor tunnels with tools like netstat and close with Ctrl+C to prevent misuse.
Security Best Practices
- Limit exposure time to minimize vulnerabilities.
- Bind tunnels to specific IPs if the remote server has multiple interfaces.
- Regularly audit SSH configurations and update software for defenses.