Secure PowerShell File Download Techniques
When downloading files via PowerShell, prioritize these security practices:
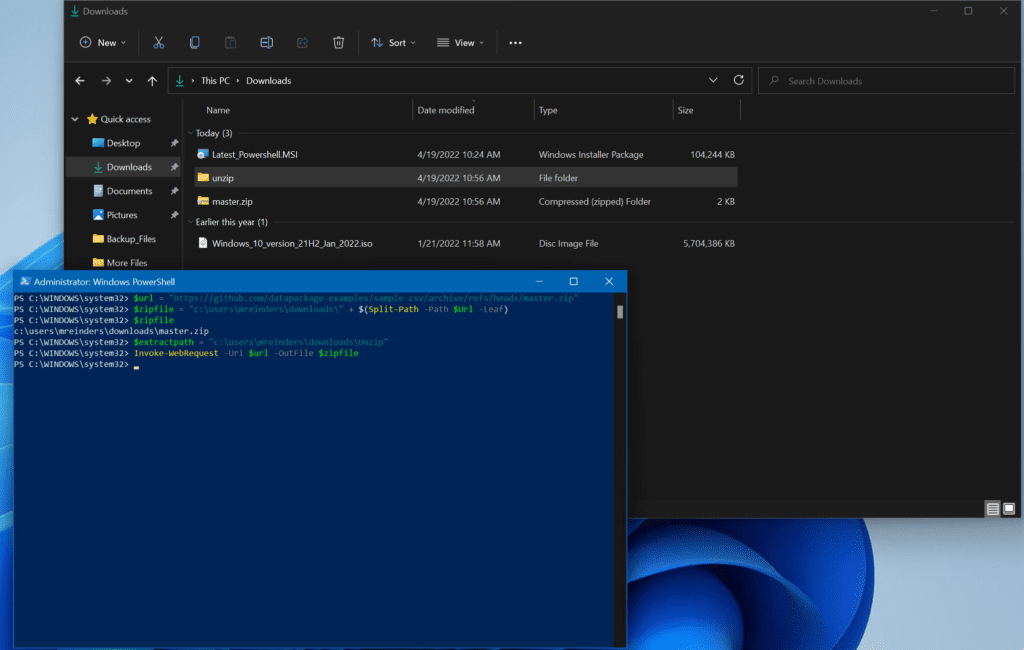
1. Enforce HTTPS and Certificate Validation
Always require encrypted connections and validate certificates using :
[*]::SecurityProtocol = [*]::Tls12
$ProgressPreference = 'SilentlyContinue'
Invoke-WebRequest -Uri "*/*" -OutFile "C:Temp*" -UseBasicParsing
- -UseBasicParsing: Disables IE engine parsing to prevent vulnerabilities
- Explicit TLS 1.2 enforcement avoids insecure fallback
2. Verify File Integrity Post-Download
Validate cryptographic hashes before execution:
$expectedHash = "3A7B1C88DCCD..."
$actualHash = (Get-FileHash -Path "C:Temp*" -Algorithm SHA256).Hash
if ($actualHash -ne $expectedHash) { Remove-Item -Path "C:Temp*" -Force }
- Always obtain hashes through separate trusted channels
- Automatically quarantine mismatched files
3. Restrict Permissions and Sandboxing
- Run downloads in constrained PowerShell sessions: * -ExecutionPolicy RemoteSigned
- Save files to isolated directories with restricted write permissions
- Block execution from temporary download paths via Group Policy
4. Alternative: Secure WebClient Method
$client = New-Object *
$*("*/*", "C:Audited*")
- Limit to simple transfers without DOM interaction
- Explicit disposal prevents memory residue leaks
Critical Security Rules
- Never bypass SSL errors (-SkipCertificateCheck creates critical vulnerabilities)
- Avoid iex (New-Object *).DownloadString() for direct script execution
- Whitelist sources via Windows Firewall: Set-NetFirewallRule -Direction Outbound
- Mandate execution policy audits: Get-ExecutionPolicy -List