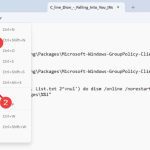
Seclookup refers to the process of querying specialized databases to retrieve cybersecurity-related information about digital entities like IP addresses, domains, email addresses, or file hashes. It enables rapid threat intelligence gathering and contextual analysis for security professionals.
Core Cybersecurity Lookup Tools
- WHOIS Lookup: Reveals domain registration details including owner, creation date, and registrar.
- DNS Lookup Tools: Map domains to IP addresses and expose associated DNS records (MX, TXT, NS).
- IP Reputation Databases: Check IP addresses against known malicious activity histories using services like commercial threat feeds.
- Hash Analyzers: Submit file hashes to platforms identifying malware variants through collective threat intelligence.
- Certificate Transparency Logs: Monitor SSL/TLS certificate issuances for suspicious domain validations.
Operational Applications
Security teams utilize these tools for:
- Investigating phishing campaigns by tracing sender IPs/domains
- Validating malware indicators during incident response
- Proactively scanning for compromised credentials in breach databases
- Assessing third-party vendor risks through infrastructure analysis
Implementation Considerations
Effective seclookup practices require:
- Cross-referencing multiple sources to reduce false positives
- Automating lookups via API integrations with SIEM/SOAR platforms
- Verifying data recency and source reliability
- Maintaining compliance with privacy regulations during investigations
These tools provide critical contextual intelligence but should complement—not replace—layered security controls like EDR and network monitoring.